It’s not all sunshine and rainbows when it comes to the internet. Undoubtedly, it’s a scary world out there when it comes to online fraud.
One of these malicious activities is “URL Phishing.” Hackers and data stealers use fake URLs that look authentic and real, but they trap the users into clicking on them.
Once you click on that phishing link, something bad will happen.
Your password, account, money, private information – something has been compromised.
Awareness is a virtue when it comes to URL phishing. The more you know, the better you’re equipped to fight this evil.
But first things first, let’s understand what URL phishing is.
What is URL phishing?
URL phishing is a malicious URL tactic to trick people into clicking on the links while posing as a legitimate source of information or the original brand that they’re trying to check out.
In some cases, hackers try to pose as a familiar brand to entice the audience to provide the users’ login details, such as usernames and passwords to get into their accounts.
Once they have access to their accounts, they can steal the info, money, or anything they want.
Sometimes, hackers create similar brands using similar domain names, logos, or business names to trick people into buying from them or providing sensitive data.
Learn about URL hijacking to be well aware of this topic.
Different types of URL phishing
Hackers and attackers trick people into clicking or downloading their files or software in different ways. It’s essential to know about several types of URL phishing that are being used to carry out these hacking attacks.
Here are different types of URL phishing users must be aware of:
Email phishing
Email phishing is a type of URL phishing in which attackers use the email medium to attack their victims. They usually send out an email to the recipient posing as a legitimate business and entice the recipient to click the link in the email before it’s too late.
Spear phishing
Spear phishing is a targeted attack aimed at an individual person in the organization, with the objective of stealing their login credentials to infiltrate the internal communication or data. The purpose of the attack is to meticulously collect information about the target, such as their name, position, and contact details, to help support the phishing attack.
Angler phishing
Angler phishing involves showcasing anger on a public forum to sound legitimate in everyone’s eyes. The attackers exploit social media platforms to engage with individuals or companies to trick them into believing in their counterfeit URLs, cloned websites, fraudulent posts, and fake tweets. These tactics aim to manipulate users into disclosing sensitive information or downloading malware.
HTTPS phishing
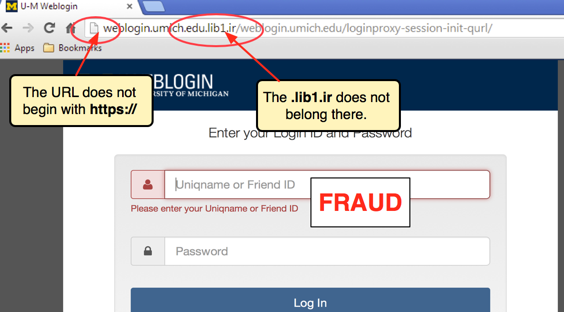
Since HTTPS provides a sigh of relief to buyers or customers when they spend money on the internet, attackers exploit the power of HTTPS to pull off their phishing attacks. The perpetrators send deceptive emails containing links to counterfeit websites with HTTPS-secured URLs. As a result, some users fall into the trap of entering their private information without doing some due diligence on this.
Related: What Does HTTP 302 Code Means For URL Shorteners?
Pharming
Code injection into the victims’ websites or blogs has been around for a long time. Pharming is a type of URL phishing that does pretty much the same thing. In fact, it involves the installation of malicious code on a victim’s computer, redirecting them to a fraudulent website designed to harvest login credentials. Therefore, a victim ends up sharing the login credentials or sensitive payment information with the hackers.
Whaling
Whaling is a type of online phishing that involves attacking a high-profile executive within an organization. Since executives have more access or privilege as compared to sub-ordinates, hackers exploit the executives’ credentials to get access to classified data or sensitive details. As a result, the organization may lose valuable information to a whaling attack.
Smishing
Smishing is a type of attack that occurs through text messages or SMS. Cybercriminals and hackers often use this phishing technique on non-tech-savvy individuals who would click on anything they get. As a result, hackers trick individuals into divulging sensitive information or downloading malicious content. It often leads to losing access to their devices or leaking sensitive data.
You May Also Like: How to Create an SEO Friendly URL: Ultimate Tips
How do phishing websites reach you?

Phishing websites reach out to users through different mediums, such as social media platforms, emails, text messages, online ads, etc.
Most URL phishing victims are new internet or mobile users who don’t have much idea about these suspicious activities.
Some scammers use URL shorteners to mask malicious links and disguise the destination link as part of their phishing tactics to deceive people.
You May Also Like: URL Masking: What Does It Mean for Marketers
Are URL shorteners safe?
Statistical data from Statista.com reports that popular URL shorteners like Bitly (53%), TinyURL (9%), Ow.ly (9%) and other URL shorteners (29%) are used for URL phishing scams.
Despite the risks involved, no one can deny the importance of short URL’s with the advent of social media platforms, revitalized communication, connectivity, and internet messaging channels.
However, there are some robust URL shorteners like Replug that keep such risks at minimum through safety checks and measures which can be used for shortening URLs.
Replug is a complete link management solution that prevents phishing scams through URL filtering, HTTPS protocol, Domain or IP Blacklisting. Also, using third party apps like URL Void, PhishTank etc., ensures safe link shortening with Replug.
The best solution for URL shortener users is to have secure short links in the form of the custom domain and white label features. Allowing users to add their own branding and creating short URLs with your own branded domains instead of Replug’s domain. Thus, it minimizes the risks of URLs being considered as spam and ambiguity of random links.
Shorten your links, amplify your brand.
Create shareable, trackable and fully customizable branded urls. Get more clicks with absolute link management features such as Bio Links, retargeting, deep Links, CTA’s and more.
Learn More!
8 ways to protect against URL phishing

It goes without saying that online security measures are crucial to your business safety and brand positioning. No brand would ever like any other brand intentionally or unintentionally appear like the original brand.
Protection against URL phishing could provide a safety net to stop hackers and intruders from stepping in and trying to get sensitive information to hijack the brand’s identity.
Here are several ways to protect against URL phishing:
1. Access only authentic URLs:
It’s understandable that we can’t verify each and every URL we visit on our phone or computer, but at least try to shop from authentic e-commerce sites and provide personal information on reliable websites. One of the ways to double-check the authenticity of a URL before clicking on it is to Google the website name or URL and see what pops up.
2. Choose a trust-worthy URL shortener:
As discussed above, URL shorteners are widely used tools by digital marketers, affiliate marketers, bloggers, and social media experts. Therefore, always opt for a well-known and safe URL-shortener.
Try to avoid clicking on random shortened links from unknown sources, especially those received in spam emails.
Branded Short Links
Create and track branded short links for your business for better conversions.
Brand Your Links Now!
3. Check for HTTPS in the domain:
HTTPS is a must-have domain security protocol for domains. Ensure the website uses HTTPS. Look for the padlock icon in the address bar, indicating a secure connection. However, it doesn’t guarantee that it’s an authentic and real website.
4. Don’t open links in unsolicited emails:
It’s vital to avoid clicking on links in emails from unknown people or unclear sources. Always ensure the legitimacy of the sender before taking any action on the email.
Related: What is URL Blacklist?
5. Enable safe browsing:
Google’s safe browsing endeavor is a savior, especially if you’re an expert on cybersecurity and URL phishing. Activate your browser’s safe browsing feature to receive warnings about potentially dangerous websites.
6. Use anti-virus software on the computer:
Install reputable antivirus and anti-malware software that provides web protection and URL blocking to block malicious URLs. It could keep your data and PC safe from any virus transfer or infiltration.
7. Install a browser security extension:
Adding browser extensions for Chrome and Firefox does help the cause to some extent. Employ a security browser extension that provides efficient browsing security. These extensions can flag potential phishing sites before you access the website.
8. Report suspected phishing activities:
To win the fight against URL phishing, actively file reports to Google, the web hosting company (that’s hosting the site), and the domain registrar that provided the domain registration service to the phishing site owner.
You May Also Like: 8 Best Ways to Fix “ERR_SSL_PROTOCOL_ERROR” for Google Chrome?
How to report a phishing URL
Let’s take a look at the most common ways to report a phishing URL:
1. Report to Google
Google’s Safe Browsing project promotes online browsing security and spreads awareness about safe browsing. The search engine giant has provided a reporting page to report phishing URLs.
To report a phishing URL, go to this page, fill up the form, and submit it to Google.
This way, the search engine would be notified about the phishing website and the team at Google would analyze the URL to determine whether or not it’s a harmful website.
Google can potentially remove the URLs from the SERP that may cause any harm to the end users or derank the specific website in the SERP.
It’s been noticed that phishing websites vanish from the SERP if reported by multiple users on the internet.
2. Report to the web host
Reporting to Google may affect the search engine ranking or organic traffic, but the website may remain active on the internet. The victim of URL phishing must take up the URL phishing case to the web hosting company.
To do this, find out about their web host and report them about the URL phishing. The legit and reputable web hosting companies take strict action against such websites, resulting in the site’s removal or account deactivation.
Site Checker is a website that allows users to find out about the web host of any given website. All you need is to put in the URL and hit the button.
Most of these websites provide accurate information on the web hosting names, IP addresses, web servers, and nameservers.
3. Report to the Domain Registrar
Besides reporting to search engines like Google and web hosting that’s hosting the phishing website, the victims can report the URL to the domain registrar.
All you need is to find a reputable Whois Lookup tool to find out about the domain registrar of the specific URL.
Whois is a popular domain information website that makes it easier for users to find out about the domain details.

It helps users find out about the domain registrar, registration date, expiration date, nameservers, and other details.
Once the victim knows where the domain is registered, such as Namecheap, GoDaddy, or any other domain registration service, they could reach out to their support team and discuss the matter with them.
The support team will require some additional verification in order to be able to take some action against the phishing website.
You May Also Like: The Importance of Choosing the Right URL Slug for SEO Success
6 Tips for identifying a phishing website
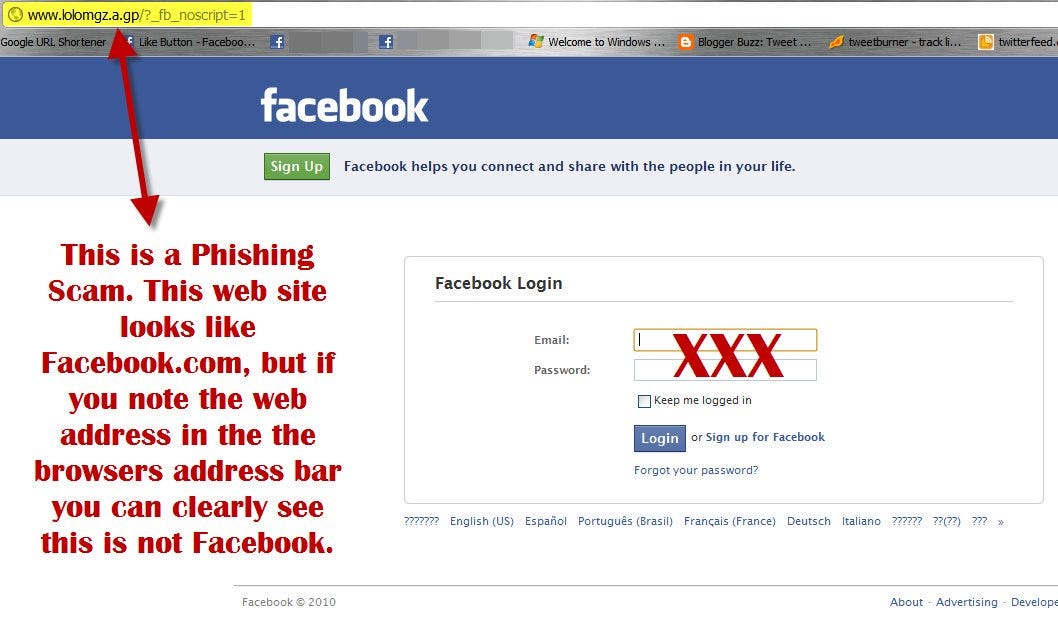
Here are a few tips on identifying a phishing website:
1. Examine the URL legitimacy
While a phishing website’s URL gives you some idea about the legitimacy of the website, it’s crucial to know other methods to identify a phishing website.
Not only do these websites use a similar brand name to a well-established business, but also try to pose as a real brand.
Always look out for the inconsistencies or misspellings in the website content. Legitimate websites typically have a consistent and correctly spelled domain name. On the other hand, phishing websites use variations or misspelled versions of legitimate domains to trick users into initiating the purchase.
You May Also Like: The Importance of Choosing the Right URL Slug for SEO Success
2. Check the brand name
Googling the brand does wonders if you know how to do a search on Google. First things first, start with typing in the brand name in Google and see what pops up. The original or legit businesses have site links, social media profiles, and brand mentions all over the SERP.
As far as the social media profiles are concerned, closely analyze the spellings. Phishing websites could also create social media accounts for the websites they’re trying to target. The easiest way to differentiate is that the original brands either have verified accounts or a rather larger audience than the fake accounts.
Furthermore, when it comes to brand mentions, the bigger the brand, the higher the number of mentions. So, it’s safe to say that googling the brand name does help in this regard.
3. Check for content quality
Don’t underestimate the power of good quality content. It’s a key differentiator between an authentic and a phishing website.
One of the best tips to identify a phishing website is the low-quality content. Legitimate blogs and websites pay close attention to putting out effective and high-quality content so that they can make an impact.
On the flip side, phishing websites don’t bother putting in the work to create good-quality content. So, anyone who knows content marketing better could tell the difference between good and bad content.
4. Read the privacy policy
Privacy policy could give you a hint about the phishing website. A trustworthy and reputed company would put in the effort to write a privacy policy so that website visitors feel safe when browsing through their site.
Whereas, a phishing website might not even have a publicly-stated privacy policy in the first place, not to mention what they say in it.
A privacy policy states how a website collects users’ information, how they make money, what the purpose of the website is, and what users should be aware of when using this website.
So, look out for the privacy policy when you’re hesitant about a specific website.
5. Watch out for the data requests
User data requests without a need are a big red flag that website visitors should be aware of when browsing through a website.
However, some legitimate companies and online tools do require integration, but these companies initiate this request upon users’ instruction. So, the users know why they should share their personal details with this company.
Attackers and hackers send out hidden data requests through emails, instant messages, and social media DMs by embedding secret codes behind the links.
When users click on the links, they end up sharing specific information with the attacker or data stealer.
6. Verify the company’s contact details
Always go the extra mile when accepting a data request or trusting someone with a link opening, especially if it’s a new contact.
It’s always best to verify the sender’s details before moving forward with your communication or data request approval.
You could always reach out to the company’s website and ask about the person who reached out to you so that you could talk to this person without any ambiguity.
You May Also Like: How to Fix Broken Links in WordPress – A Complete Guide
Popular Examples of URL phishing
Let’s take a look at some of the URL phishing example cases:
1. Facebook and Google were scammed by a fake vendor
According to a CNBC article, Facebook and Google were tricked out by a phishing scam, which resulted in a loss of $100 million between 2013 and 2015. The phishing scam was pulled off as the scammer posed as Quanta, a vendor that is used by both Facebook and Google.
The scammer sent fraudulent invoices posing as Quanta to both Facebook and Google and got paid. The fraud was eventually uncovered, leading to legal actions initiated by Facebook and Google in the United States.
2. FACC BEC scam
An article reported a $61 million fraud at an Austrian aerospace parts manufacturer that fell victim to a BEC scam. The phisher tricked an accounts department employee by impersonating the CEO of the company and directing the employee to transfer funds to an attacker-controlled account.
FACC took the unusual step of terminating and suing its CEO and CFO, seeking $11 million in damages for their failure to implement adequate security measures afterward.
3. Amazon Prime Day phishing scam
AstrillVPN shared the phishing scam in a blog post on their website. In October 2021, attackers launched a phishing scam campaign targeting online shoppers during Amazon Prime Day 2021. The phishing email claimed to provide exclusive access to the offers. When users took action on the offer, they were redirected to a different website asking for login credentials and other personal information.

Create Safe, SSL Encrypted & Secure Short Links With Your Own Custom Domain
Replug scans and checks links in real-time, blocks malicious URLs, and uses phishing detection algorithms to assure safety measures. Protecting you and your customers from possible threats and harmful data.
FAQS about URL phishing
Let’s answer some of the frequently asked questions about the phishing URLs:
What does a phishing URL look like?
A phishing URL may look like any other legitimate URL, but it may ask you for login credentials or payment information. Moreover, most phishing URLs try to pose like a popular brand. Watch out for the domain spellings and company logos to identify a phishing website.
What makes a URL suspicious?
Any URL that looks like a popular brand’s URL or appears to be the original brand is a red flag. Sometimes, scammers create websites with the same name as other companies with a different extension to fool the customers.
What happens if you click on a phishing link?
When you click on a phishing link, you’re most likely to provide some kind of access to your login credentials, financial information, or other sensitive data, which shouldn’t be shared with anyone.
Companies respond very quickly if they sniff a little bit of breach in the users’ data and reach out to the users/customers to change their account security protocols, such as password, passcode, or secret question.
How do you know if you have been phished?
While clicking on the unknown links from someone you don’t know or they don’t seem like a real business could be dangerous, it’s difficult to know initially when it happens unless you have taken security measures to catch these phishing activities.
Most users find out about phishing attacks when they see order confirmations in their inbox or suspicious activities in their credit card statements.
Software companies, SAAS tools, and financial apps have security protocols that allow them to quickly detect such illegal and malicious activities and they immediately block out the compromised accounts until the problem is resolved.
How do I know if a URL is safe?
Google the same URL and see if other pages show up in the SERP. Also, type in a search query, “site:URL” and see what pops up. If you see only a couple of dozen pages for a large website, then you should be very careful about it. Moreover, you can check out the pages, such as About, Company Profile, Contact, and Services/Products to analyze the authenticity of the site.




































